You have invested so much time into crafting your Magento eCommerce website so it can be an enjoyable experience for your customers, and the last thing you need is a possible security breach. Avoid the unnecessary risks by installing the latest Magento patch SUPEE-6285 and understanding what site security threats to watch for.
MAGENTO SECURITY PATCH SUPEE-6285
The newest patch SUPEE-6285 was released on July 7th and addresses a variety of security issues from injection attacks, to requesting forgeries and cross-site scripting, to ACL permissions for third-party extensions. This patch comes at an interesting time, following concerns brought to light by Sucuri over credit card scrapers. Magento’s Ben Marks promptly responded about the impact of these issues, and the timing is most likely just a coincidence.
Two of the larger issues that this patch addresses are template injection attacks and automatic logging file permissions.
Before this security patch, any theme file that overwrote these base template files was vulnerable to unescaped HTML injection attacks.
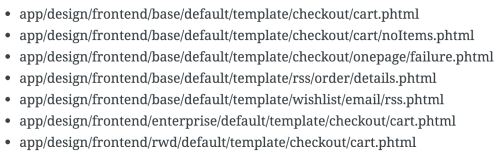
Injection attacks allow undesirable code to be executed on your webserver, usually through a parameter value. This opens up the possibility for secure information to be displayed on these pages. If any of these templates have been customized, you’ll need to make sure the changes are included in your custom package/theme files.
File Permissions have been a standing issue in stores that have logging enabled. Magento automatically creates the log folders if they don’t exist. Originally, these folders were given full Read, Write and Execute permissions. With these changes, the folders are given more secure permissions from the get-go.
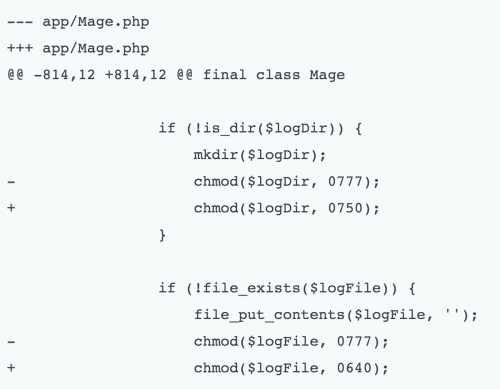
For a full breakdown and write-up of all the changes in the SUPEE-6285 patch, check out this great overview by Phillip Jackson, and for details on all patch releases, check out Magento’s resources.
WHY YOU SHOULD TAKE MAGENTO SECURITY PATCHES SERIOUSLY
Version upgrades and patch releases are a core part of Magento’s ongoing commitment to excellence in security. Magento is constantly striving to improve their performance, and one important aspect towards developing a positive experience for Magento customers is providing top-of-the-line security. Although Magento provides security updates, the only way to guarantee the safety of your site is to utilize their resources and take the proper security measures.
If you are running a piece of web application software and you are doing eCommerce, it’s your responsibility to keep up to date with security measures not only to ensure safety of your website, but for the safety of your customers, too.
Additionally, you want to make sure you are PCI compliant, that there are no security holes in your server configuration and that your SSL Certificate encryption is up to date. These are all aspects that fall under your responsibility when running an eCommerce store. After all, you definitely don’t want to end up with the negative impacts of a site hack.
WHERE TO GO TO LEARN MORE ABOUT MAGENTO SECURITY
Magento has always been good about sending notifications to Admins to make them aware of updates, but they haven’t always been clear about the details in the updates. Moving forward, Magento is making it a priority to be as transparent as possible by disclosing all issues patched in every new security release or patch.
(If you for some reason aren’t getting Magento security patch alerts emailed to you, I highly suggest signing up for the security alert registry now.)
If you’re also having a hard time installing the new Magento patch, learn how to install it step by step here.
Interested in learning about other Magento software updates and the benefits of working with a Magento Gold Partner? Contact us today! Our Magento-certified Developers would love to help.

